🧑🚀 全世界最好的 llM 资料总结(数据处理、模型训练、模型部署、 O1 模型、 MCP 、小语言模型、视觉语言模型) | Resumen de los mejores recursos del mundo.

mcpauth
MCP Gateway para autenticación y autorización externa
0
Github Watches
0
Github Forks
0
Github Stars
MCPAuth
MCPAuth: Gateway Authentication for Secure Enterprise MCP Integrations



🔐 MCPAuth: Gateway Authentication for Secure Enterprise MCP Integrations
McpAuth is the authentication and authorization component of the MCP Gateway Proof of Concept (PoC) described in the paper:
Simplified and Secure MCP Gateways for Enterprise AI Integration
Ivo Brett, CISSP, B.Eng, MSc
View Paper (2025)
This repository is part of a broader initiative to enable secure, scalable, and compliant enterprise integration with the Model Context Protocol (MCP). It provides an extensible OAuth2.1-based authentication gateway that offloads identity, authorization, and policy management from backend MCP servers—ensuring conformance with the 2025-03-26 MCP Specification.
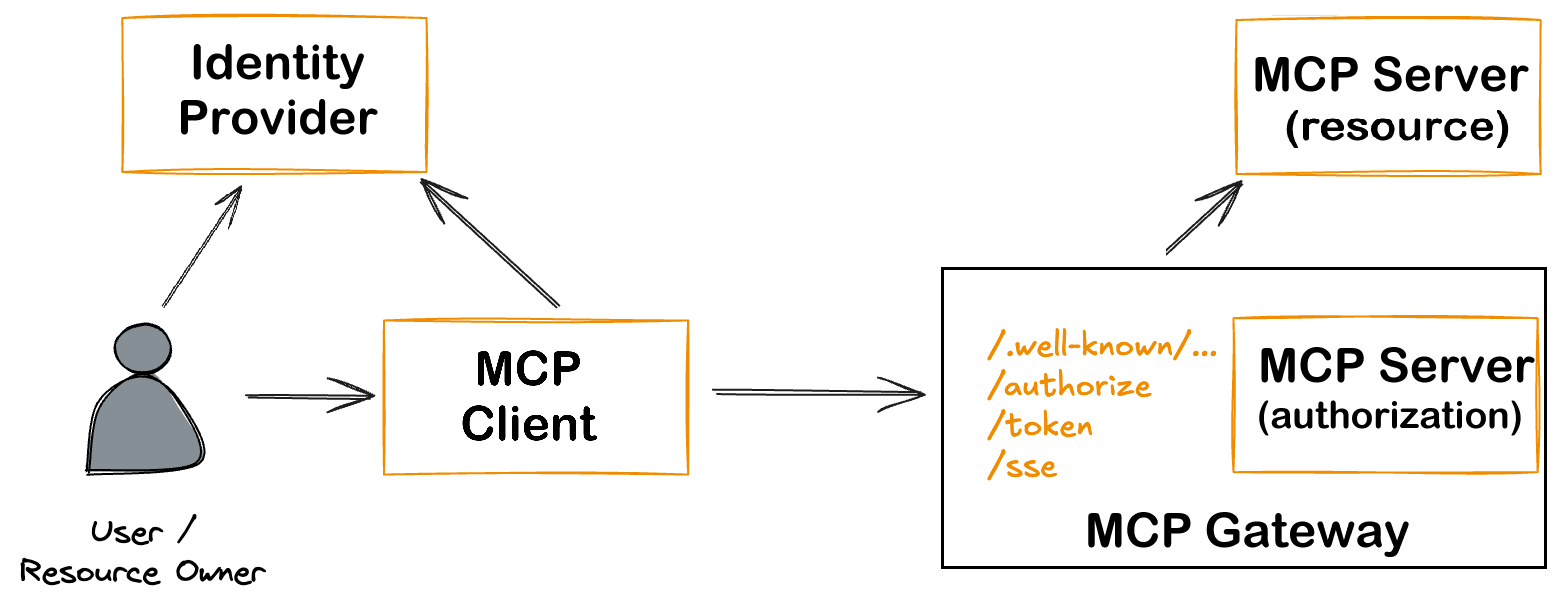 ---
---
🔍 Purpose
McpAuth is designed to:
- Decouple security logic from MCP servers
- Centralize identity management using OAuth 2.1 & OIDC
- Support dynamic client registration
- Enforce fine-grained token scopes and policy controls
- Act as a composable module in enterprise-grade Zero Trust architectures
📚 Background
This implementation is part of a larger PoC that validates:
- A reference MCP Gateway architecture for secure deployments
- Threat model mapping aligned with frameworks such as MAESTRO and Narajala & Habler
- Real-world compatibility with tools like Cloudflare Tunnels, WireGuard, Traefik, and CrowdSec
The full proof of concept includes:
- Two isolated MCP servers (local and cloud-based)
- Secure tunneling via WireGuard and Pangolin
- Centralized intrusion detection and observability
- Seamless integration with Anthropic's MCP Inspector
✨ Features
- 🔐 OAuth2 authentication with PKCE via Traefik
forwardAuth - ⚡ Seamless integration with MCP Gateway SSE endpoints
- ✅ Email whitelisting for controlled access
- 🐳 Docker-ready, easy to deploy
- 🧪 Includes a Python-based test server
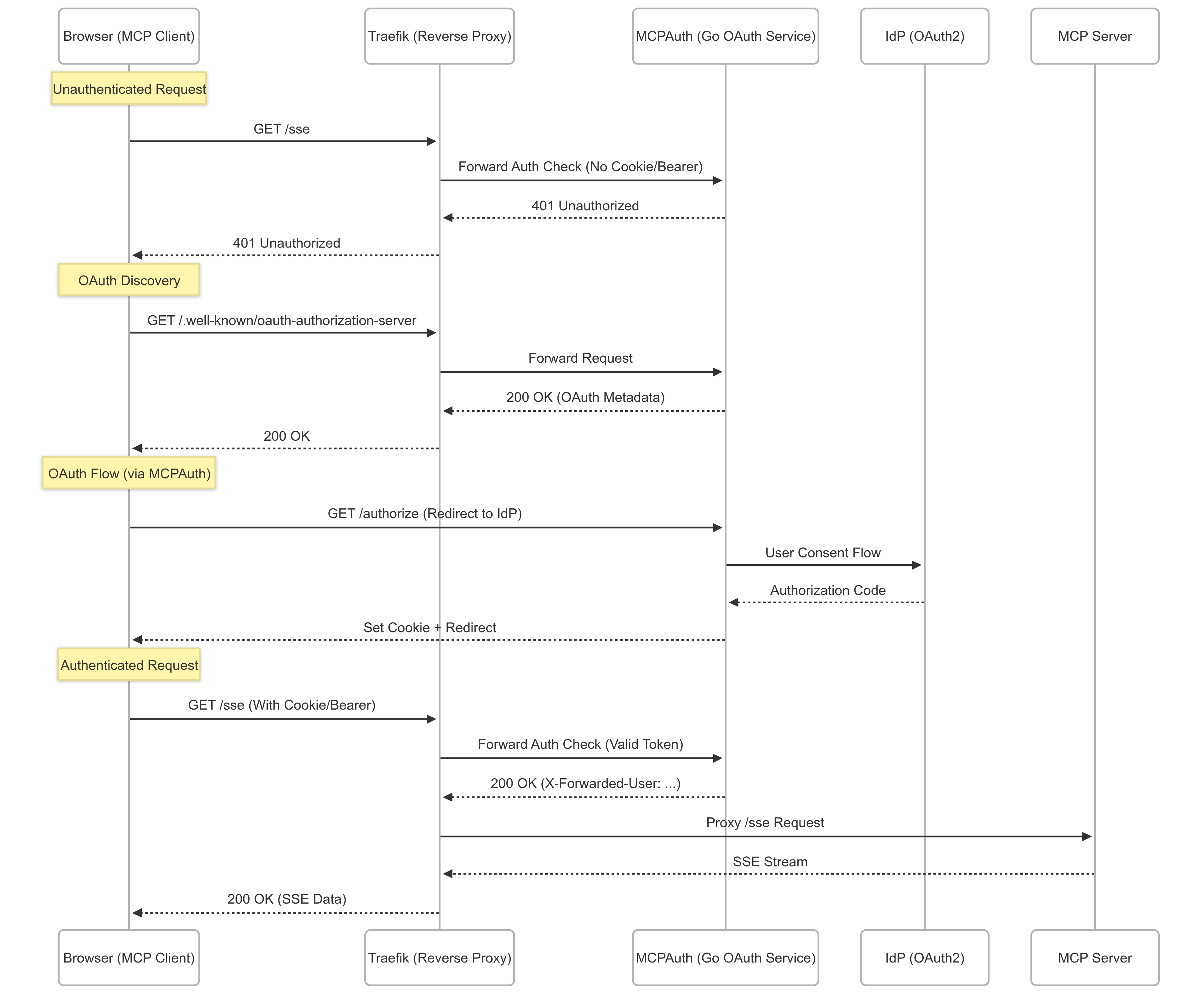
🚀 Quick Start
📦 Prerequisites
- Go 1.21+
- Traefik v2.x+
- An OAuth provider (e.g., Google, GitHub)
🛠️ Installation
git clone https://github.com/oidebrett/mcpauth
cd mcpauth
go mod tidy
🔧 Configuration
Use flags or environment variables:
| Variable | Default | Description |
|---|---|---|
PORT |
11000 |
Port for the auth server |
PROTECTED_PATH |
/sse |
Protected endpoint path |
OAUTH_DOMAIN |
(none) | OAuth issuer domain |
CLIENT_ID |
(none) | OAuth client ID |
CLIENT_SECRET |
(none) | OAuth client secret |
ALLOWED_EMAILS |
(none) | Comma-separated list of allowed emails |
LOG_LEVEL |
1 |
0=debug, 1=info, 2=minimal |
go run cmd/main.go -port=11000 -oauthDomain=your-domain.com
🐳 Docker Deployment
Basic Docker Compose
services:
mcpauth:
build: .
environment:
- PORT=11000
- CLIENT_ID=${CLIENT_ID}
- CLIENT_SECRET=${CLIENT_SECRET}
ports:
- "11000:11000"
🔐 Traefik Integration
ForwardAuth Middleware
http:
middlewares:
mcp-auth:
forwardAuth:
address: "http://mcpauth:11000/sse"
authResponseHeaders:
- "X-Forwarded-User"
Attach to a Router
labels:
- "traefik.http.routers.myapp.middlewares=mcp-auth@file"
🧪 Testing
Run Included Test Server
cd test_mcp_server
python3 -m venv venv
source venv/bin/activate
pip install -r requirements.txt
python mcp-server-sse.py
With curl
curl -i http://localhost:11000/health
curl -i http://localhost:11000/sse
🧱 Middleware Chain (Traefik)
Apply middlewares in this order:
-
mcp-cors-headers -
redirect-regex -
mcp-auth
Example dynamic config:
http:
middlewares:
mcp-cors-headers:
headers:
accessControlAllowCredentials: true
accessControlAllowHeaders:
- Authorization
- Content-Type
- mcp-protocol-version
accessControlAllowMethods:
- GET
- POST
- OPTIONS
accessControlAllowOriginList:
- "*"
accessControlMaxAge: 86400
addVaryHeader: true
redirect-regex:
redirectRegex:
regex: "^https://([a-z0-9-]+)\\.yourdomain\\.com/\\.well-known/oauth-authorization-server"
replacement: "https://oauth.yourdomain.com/.well-known/oauth-authorization-server"
permanent: true
mcp-auth:
forwardAuth:
address: "http://mcpauth:11000/sse"
authResponseHeaders:
- X-Forwarded-User
🧠 Middleware Manager Support
This project supports middleware-manager.
Example templates.yml:
middlewares:
- id: mcp-auth
name: MCP Authentication
type: forwardAuth
config:
address: "http://mcpauth:11000/sse"
authResponseHeaders:
- "X-Forwarded-User"
- id: mcp-cors-headers
name: MCP CORS Headers
type: headers
config:
accessControlAllowMethods:
- GET
- POST
- OPTIONS
accessControlAllowOriginList:
- "*"
accessControlAllowHeaders:
- Authorization
- Content-Type
- mcp-protocol-version
accessControlMaxAge: 86400
accessControlAllowCredentials: true
addVaryHeader: true
- id: redirect-regex
name: Regex Redirect
type: redirectregex
config:
regex: "^https://([a-z0-9-]+)\\.yourdomain\\.com/\\.well-known/oauth-authorization-server"
replacement: "https://oauth.yourdomain.com/.well-known/oauth-authorization-server"
permanent: true
📜 License
Licensed under the GNU General Public License v3.0.
相关推荐
AI's query engine - Platform for building AI that can answer questions over large scale federated data. - The only MCP Server you'll ever need
🔥 1Panel proporciona una interfaz web intuitiva y un servidor MCP para administrar sitios web, archivos, contenedores, bases de datos y LLM en un servidor de Linux.
Reviews
user_q236EbmN
As a dedicated user of the MCP app ecosystem, I can confidently say that mcpauth by oidebrett is an essential tool for anyone looking to streamline their communication and authentication processes. Its robust features and seamless integration have significantly improved my workflow, making it a must-have for any professional. Highly recommended!
user_QXnbYVIQ
As a devoted MCP user, I absolutely love mcpauth by oidebrett! This product seamlessly integrates with my existing applications, making authentication processes a breeze. The user-friendly interface and detailed documentation make setup quick and easy. Highly recommend it!
user_UNZcdaRR
As a dedicated user of MCP applications, I must say that mcpauth by oidebrett is an indispensable tool. Its seamless integration and ease of use make authentication processes a breeze. If you're looking for reliability and efficiency, this is definitely the go-to solution. Highly recommended!
user_hobfibX4
I've been using mcpauth by oidebrett, and it's truly a fantastic tool! The authentication process is seamless and reliable, making security management much easier. The documentation is clear, and the support from the community is top-notch. Highly recommend for anyone looking for a robust authentication solution.
user_cyIjD7xm
As a loyal user of MCP applications, I must say mcpauth, authored by oidebrett, has been a game-changer. The seamless integration and user-friendly interface make authentication easy and secure. The comprehensive documentation and stellar support enhance the overall experience. Highly recommend!
user_jbTLKtvu
As a dedicated user of MCP applications, mcpauth is an exceptional tool created by oidebrett. Its seamless integration and user-friendly interface make authentication processes smooth and efficient. I highly recommend mcpauth to anyone in need of a reliable authentication solution. Its consistent performance and robust features have greatly enhanced my workflow.
